Unlock the intricate world of illicit financial activities as we delve into the depths of money laundering. From understanding the fundamentals to unraveling the sophisticated schemes employed by criminals, this article is your gateway to comprehending the clandestine realm of financial deception. Join us on a journey that exposes the methods used to ‘place,’ ‘layer,’ and ‘integrate’ illicit funds, offering insights into the key strategies employed to conceal the proceeds of crime. From offshore accounts to false invoices, we demystify the complex landscape of money laundering, shedding light on crucial anti-money laundering obligations. Dive into this informative guide and equip yourself with the knowledge to navigate the complexities of financial deceit.
Money Laundering Schemes
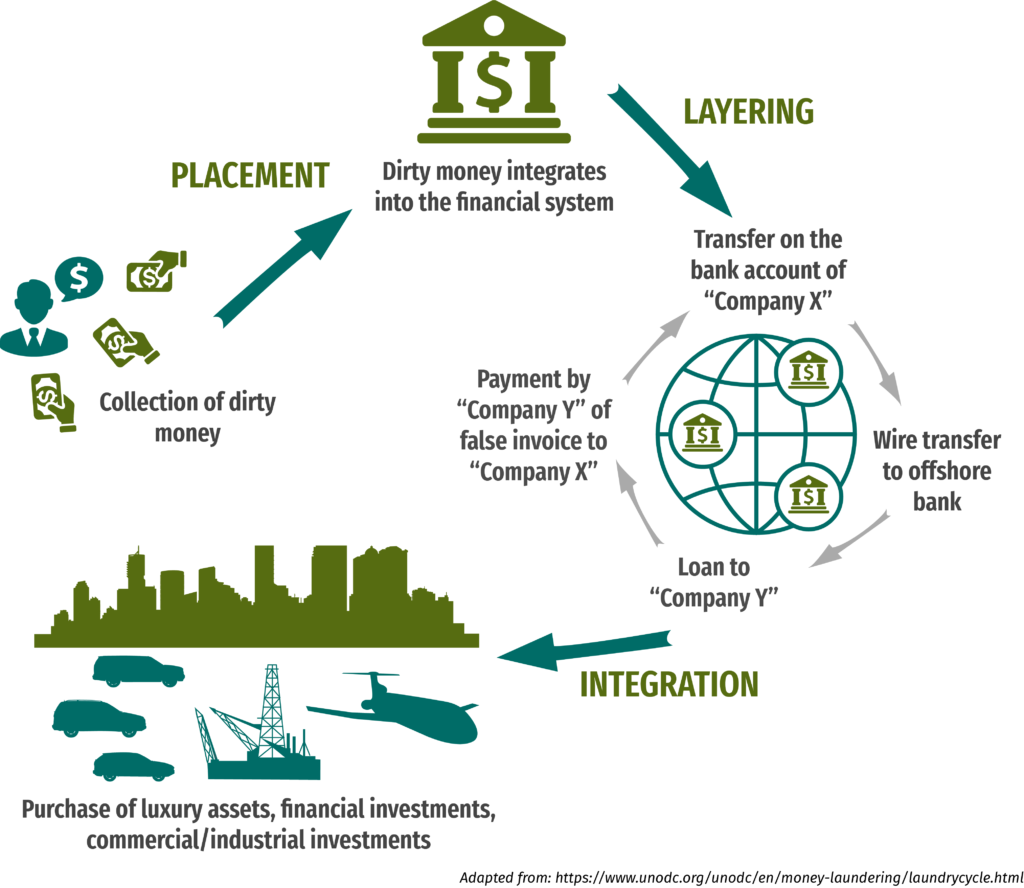
How do money laundering schemes work?
Money laundering schemes are sophisticated maneuvers designed to conceal the true origin of illicit funds. Criminals employ various tactics to blur the financial trail, making it challenging for authorities to trace and apprehend them. Understanding the intricacies of these schemes is crucial for identifying and thwarting illicit financial activities.
Examples of money laundering schemes
Examining real-world examples provides insight into the diversity and adaptability of money laundering schemes. From complex corporate setups to seemingly legitimate transactions, criminals exploit various avenues to legitimize their ill-gotten gains. These examples serve as cautionary tales, illustrating the importance of vigilance in detecting and preventing money laundering.
What businesses are used for money laundering?
Money launderers often exploit businesses as conduits for their illegal activities. Whether through shell companies, front businesses, or legitimate enterprises manipulated for criminal purposes, understanding the types of businesses frequently involved in money laundering is essential. Recognizing these patterns is a crucial step in fortifying anti-money laundering measures. This exploration into money laundering schemes delves into the modus operandi employed by criminals, offering a comprehensive understanding of the tactics and businesses entangled in these illicit financial activities. Stay tuned to unravel the intricacies of financial deceit and fortify your defenses against the shadowy world of money laundering.
Methods of ‘Placement’
How criminals ‘place’ money into the financial system
The initial stage of money laundering, known as ‘placement,’ involves introducing illicit funds into the legitimate financial system. Criminals employ various tactics, such as making small, inconspicuous deposits, using cash-intensive businesses, or engaging in high-frequency transactions to obscure the origins of the funds. Understanding these placement methods is crucial for detecting and preventing the infiltration of dirty money into the financial mainstream.
Blending of funds
To further obfuscate the paper trail, money launderers engage in blending funds. This technique involves mingling illicit funds with legitimate ones, making it challenging to distinguish between clean and tainted money. By camouflaging their activities within the vast sea of financial transactions, criminals aim to divert attention from their unlawful activities.
‘Smurfing’
‘Smurfing’ is a technique where large sums of illicit money are broken down into smaller, less conspicuous amounts. These smaller amounts are then deposited separately to evade suspicion. The term ‘smurfing’ aptly captures the clandestine nature of this method, as criminals seek to stay under the radar by dividing and conquering the financial system.
Invoice fraud
In the world of money laundering, invoice fraud is a common tactic. Criminals create fictitious invoices or manipulate existing ones to legitimize the movement of illicit funds. This deceptive practice often involves collusion with businesses, creating a veneer of legitimacy around the illicit financial transactions.
Offshore accounts
Money launderers frequently utilize offshore accounts to further distance themselves from the illicit funds. Offshore jurisdictions, known for their confidentiality and lax regulations, provide a favorable environment for criminals to conceal the true ownership of funds and complicate the investigative process.
Aborted transactions
Aborted transactions involve initiating a financial transaction and intentionally stopping it before completion. This tactic adds a layer of complexity, as authorities may find it challenging to trace and investigate transactions that never fully materialize. Money launderers exploit this ambiguity to navigate through the financial system undetected. Understanding the methods of ‘placement’ in money laundering sheds light on the initial stages of the illicit financial journey. Stay with us as we navigate through the subsequent layers of ‘layering’ and ‘integration,’ unraveling the comprehensive landscape of money laundering schemes.
Techniques of ‘Layering’
How ‘layering’ conceals the proceeds of crime
After successfully placing illicit funds into the financial system, money launderers move on to the ‘layering’ stage. Here, the objective is to create intricate layers of financial transactions to obscure the origin and ownership of the tainted money. This phase involves a series of complex maneuvers aimed at confusing investigators and veiling the illicit funds within a web of legitimate transactions.
Moving money across borders electronically
Money launderers leverage electronic transfers to move funds across borders swiftly. Utilizing digital channels and cryptocurrencies, they exploit the global nature of financial systems to complicate the tracking of transactions. The speed and anonymity of electronic transfers make them a preferred tool for layering, enabling criminals to disperse funds across multiple jurisdictions.
Converting funds into financial instruments
In the layering process, criminals often convert illicit funds into financial instruments like stocks, bonds, or derivatives. This transformation not only complicates the audit trail but also allows criminals to potentially generate additional revenue through the legitimate financial market. Layering through financial instruments adds complexity to the investigation, as authorities must navigate the intricacies of diverse financial products.
Investing in companies with a functional front
Money launderers may choose to invest illicit funds into seemingly legitimate businesses. These companies, known as ‘functional fronts,’ operate genuinely on the surface, concealing the illicit source of their financial backing. By infiltrating various industries, criminals perpetuate the illusion of legitimate economic activities, making it challenging for investigators to discern the genuine from the illicit.
Understanding the techniques of ‘layering’ is essential in comprehending the sophistication behind money laundering schemes. As we unravel the intricate layers employed by criminals, the next segment will delve into the strategies of ‘integration,’ exposing how these ill-gotten gains seamlessly merge with the legitimate economy. Stay with us to uncover the final stages of the money laundering process.
Strategies of ‘Integration’
How ‘integration’ disguises the source of funds
In the final stage of money laundering, ‘integration’ aims to seamlessly merge illicit funds with the legitimate economy, making them indistinguishable from legally obtained resources. This strategic phase involves investing tainted money into various assets and financial activities, ensuring that the proceeds of crime become an integral and inconspicuous part of the economic landscape.
Investing in assets
Money launderers strategically invest in tangible assets such as real estate, luxury goods, or valuable commodities. By acquiring these assets, criminals not only secure their ill-gotten gains but also introduce a layer of legitimacy. Real estate, in particular, provides a convenient avenue for integration, as property holdings can be difficult to trace and offer a tangible asset that retains value.

Raising false invoices
Another method employed in the integration phase is the creation of false invoices within seemingly legitimate business transactions. Criminals may establish sham companies or manipulate existing ones to generate invoices for non-existent goods or services. These fictitious transactions introduce a semblance of legitimate economic activity, masking the true origin of the funds.
Understanding the strategies of ‘integration’ is crucial for authorities and businesses to identify potential money laundering activities. As we conclude our exploration into the complex world of money laundering. The next segment will highlight key anti-money laundering obligations. By staying informed and vigilant, individuals and organizations can contribute to a collective effort against financial crime. Join us as we unravel the final layers of this intricate financial web.
Preventing Money Laundering
Key Anti-Money Laundering Obligations
To counter the intricate web of money laundering, governments and financial institutions worldwide enforce stringent Anti-Money Laundering (AML) obligations. These measures are designed to detect and prevent illicit financial activities, safeguarding the integrity of the financial system. Understanding these key AML obligations is essential for both financial institutions and businesses to comply with regulations and contribute to the global fight against money laundering.
Anti-money laundering made easy
Compliance with AML regulations may seem daunting, but various resources and tools make the process more manageable. Governments and regulatory bodies often provide comprehensive guidelines to assist businesses in implementing effective AML policies. Furthermore, advancements in technology have given rise to sophisticated AML software, simplifying the identification of suspicious transactions and ensuring adherence to regulatory requirements.
By embracing and upholding these AML obligations, financial institutions and businesses play a pivotal role in disrupting the money laundering cycle. This final section of our exploration underscores the collective responsibility to fortify defenses against financial crime. Stay with us as we conclude our journey, armed with insights into the preventive measures that form a crucial line of defense in the ongoing battle against money laundering.
Cost-Efficient AML Compliance
Cut Costs on AML Compliance – Download Our Free Guide
Amid the imperative to combat money laundering, businesses face the challenge of implementing effective Anti-Money Laundering (AML) measures without incurring exorbitant costs. Recognizing this, there’s a growing focus on cost-efficient AML compliance strategies. In this section, we explore how businesses can navigate the complex landscape of AML requirements without breaking the bank
Embracing Technological Solutions
Technology emerges as a powerful ally in cost-efficient AML compliance. Automated solutions, leveraging artificial intelligence and machine learning, streamline the identification of suspicious activities. These technologies not only enhance the accuracy of risk assessments but also reduce the manual workload, allowing businesses to allocate resources more efficiently.
Collaborative Efforts and Shared Resources

In the fight against money laundering, collaboration proves to be a cost-effective strategy. Sharing AML resources and intelligence within industries or through regulatory bodies enhances the collective ability to identify emerging threats. By pooling knowledge and resources, businesses can fortify their defenses without duplicating efforts, resulting in a more efficient and cost-effective AML landscape.
Educational Initiatives for Staff
Investing in the education and training of staff is a proactive and cost-effective approach to AML compliance. Well-informed employees are better equipped to identify suspicious activities and adhere to AML protocols. By fostering a culture of awareness and vigilance, businesses create a front line defense against potential money laundering risks.
Regulatory Technology (RegTech) Solutions
The emergence of Regulatory Technology, or Reg Tech, presents a cost-effective avenue for AML compliance. These specialized technologies are tailored to meet regulatory requirements, offering businesses scalable and efficient solutions. RegTech solutions not only reduce the burden of compliance but also ensure adaptability to evolving AML regulations.
Strategic Risk-Based Approach
Adopting a risk-based approach to AML compliance enables businesses to allocate resources where they are most needed. By focusing efforts on high-risk areas and customers, organizations can optimize their AML strategies, ensuring a more cost-efficient and targeted response to potential threats.
Navigating the realm of AML compliance need not be a financial burden. By embracing technology, fostering collaboration, investing in education, and strategically allocating resources, businesses can achieve effective AML measures without compromising financial stability. In our final segment, we invite you to download our free guide, offering valuable insights into cutting costs on AML compliance. Join us as we conclude our exploration into the intricacies of money laundering prevention.
Conclusion
In the ever-evolving landscape of financial security, this exploration into money laundering and cost-efficient Anti-Money Laundering (AML) compliance unveils a proactive blueprint for businesses and institutions. From unravelling the intricate layers of money laundering schemes to embracing technological solutions and collaborative efforts. The collective journey has been one of enlightenment and empowerment. As we conclude, armed with insights into key AML obligations and cost-effective strategies. Businesses are poised to fortify their defenses against the persistent threat of financial crime. Our commitment to a vigilant and informed approach marks a crucial step in disrupting the cycles of money laundering and ensuring the integrity of the global financial system. Download our free guide to cutting costs on AML compliance, and let us collectively stride forward into a future where financial security is a shared responsibility and a well-protected reality.

